Meet the Ethical Hacker that never clocks out of work
This is how Artificial Hackers keep critical assets secured 24/7
Finds and prioritizes your vulnerabilities with
<0.5% false positives
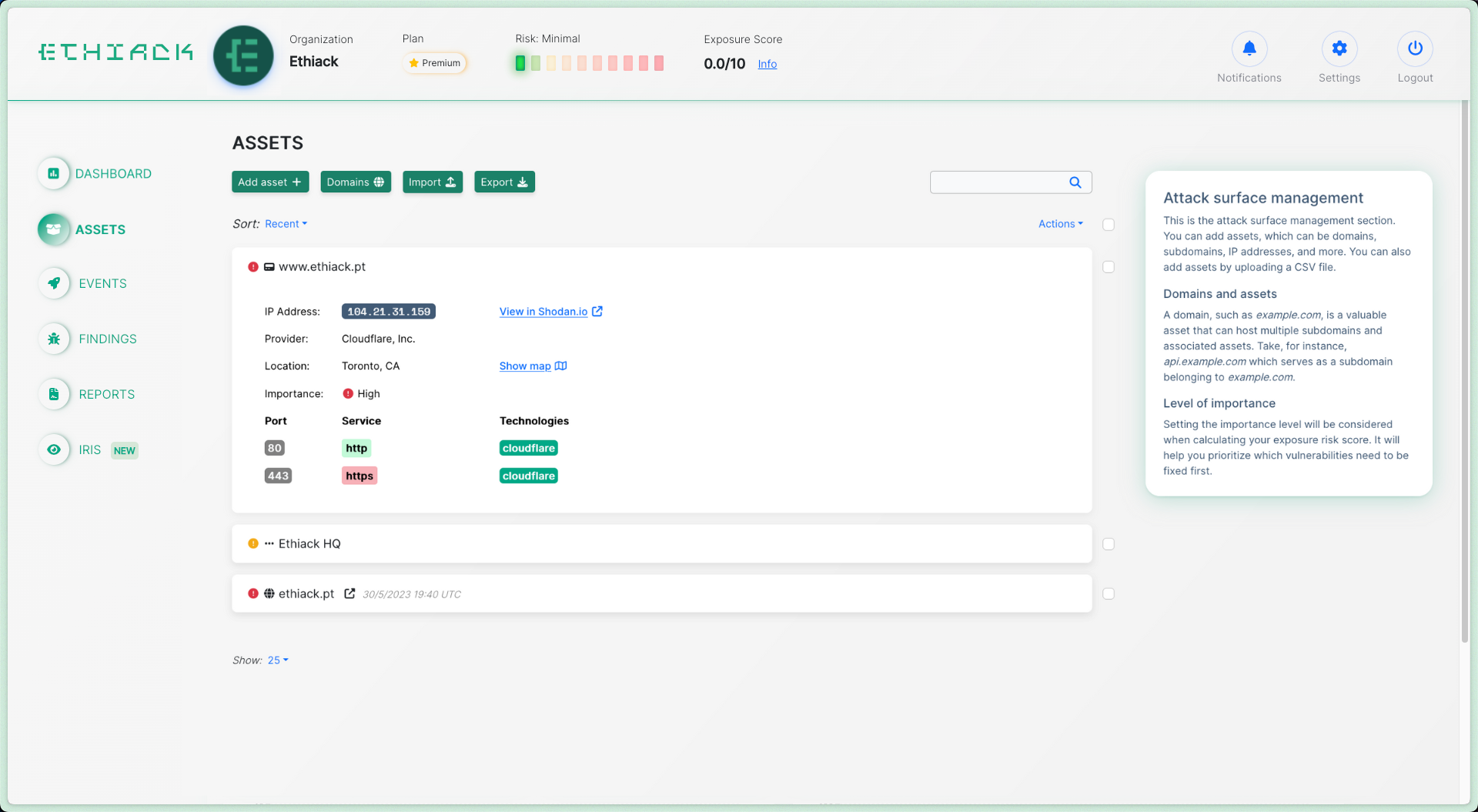
To secure your digital infrastructure, our technology maps all of your digital assets, tests them, and lets you know which vulnerabilities you should fix first.


Testing for thousands of vulnerabilities
Artificial Hackers learn new attack vectors from open-source and proprietary sources, as well as manual additions from our R&D team.
Over 60,000 findings submitted
Advanced attack patterns with multi-step approaches
AI-Powered detection of new vulnerabilities
Learns from past attacks to reduce false positives and improve attack vectors
Human and machine,
hacking together
The best defense comes from combining the speed of machines with the knowledge of humans. Our symbiotic approach delivers the best results for security teams.
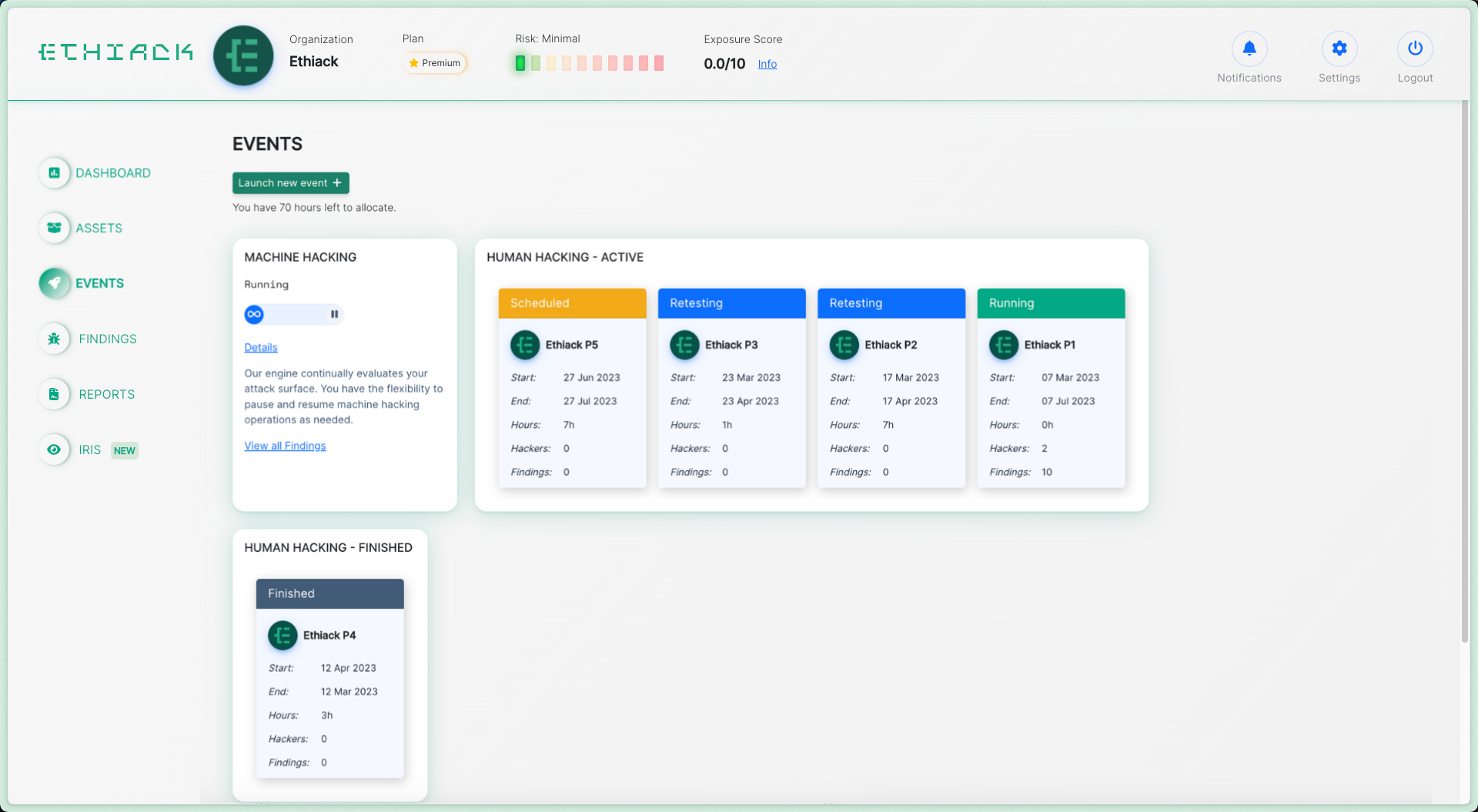
Artificial hackers perform in-breadth, continuous testing
Ethical Hackers find complex attack vectors in your in-scope assets
Results from the Artificial Hackers and the Ethical Hackers improve our AI Engine to make future Automated Pentesting better
How the ARTIFICIAL HACKERS work
<0.5% false positives on reported findings
Each finding comes with a detailed report on how to reproduce and mitigate the vulnerability.
24/7 Monitoring and Testing your Assets
Whenever changes occur in your environment, our Artificial Hackers get to work. They act based on events so they don’t overload your infrastructure, reducing costs.
Hacking Learning Engine
Powered by AI
Artificial Hackers learn from past attacks to generate new modules when vulnerabilities are found. They are being constantly updated on new technologies, reducing your chances of malicious exploitation.
Begin testing
by adding your first Domain

ADD THE ETHIACK TXT RECORD

ARTIFICIAL HACKERS TEST YOUR ASSETS
GET REPORTS ON HOW TO FIX VULNERABILITES
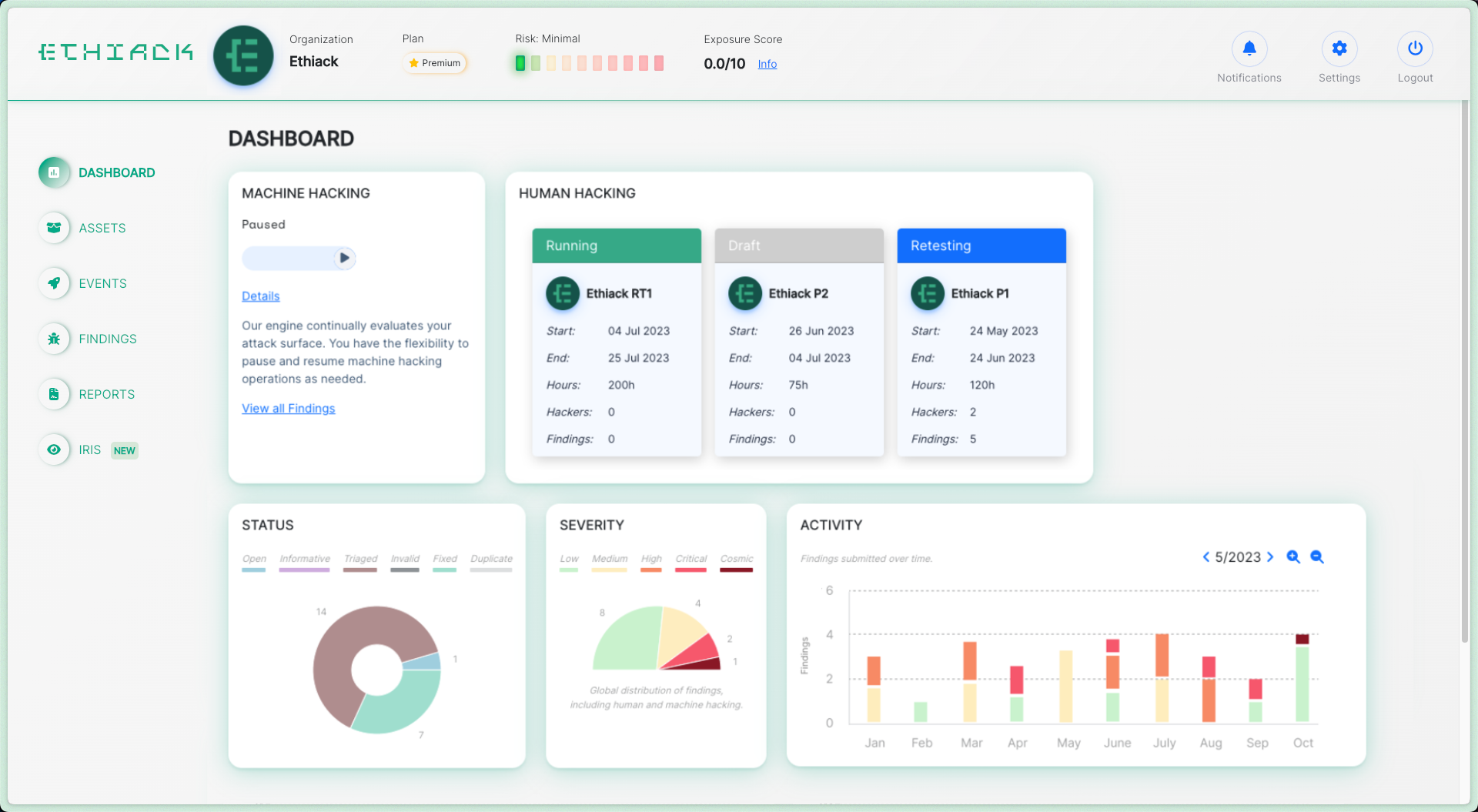
Manage your Security work
from one place
Use Automated Pentesting to
protect your digital assets
Get started with a 30-day free trial.
Launch your first AI Automated Pentesting event in the next 5 minutes.